Building Sustainable Business Models for System of Systems Architectures: Success Factors for Customers and Industry

Welcome to the first article in our Proving Ground’s Embracing Innovation series. Our Embracing Innovation articles will explore how defense industry must embrace and shape evolving CONOPs, acquisition approaches, and business models to drive growth in the era of strategic competition.
The Defense Department is in the middle of a far-reaching transformation in how it develops and acquires capabilities to deter and defeat near peer threats.
It has interrupted the traditional requirements process for several next-generation programs in favor of system of systems architectures that aim to create resilient operational capabilities, rather than a discrete platform or program.
This model fundamentally challenges traditional industry value creation models – successful operationalization of system of systems architectures will require the Department and its industrial partners to transform policies, behavior, and culture.
Background on System of Systems Architectures:
Emerging system of systems architectures span diverse missions, but are unified by principles of disaggregation, information networking, and automated fusion.
Each architecture is intended to devolve into multiple acquisitions, procured separately but coordinated centrally to achieve a collective mission capability.
These principles are not new, but only recently have technology advancements, acquisition structures, and decentralized mission command principles combined to create momentum.
Joint All-Domain C2 is the most visible example. It encompasses the integration of each Service’s multi-domain operations concepts, which have percolated for years at doctrinal and even operational levels as in the case of the Navy’s Cooperative Engagement Capability.
The Air Force’s Advanced Battle Management System receives the most attention, but each of the Services is maturing its JADC2 contributions.
In addition, many other Defense Department initiatives are built on SoS principles – these include high-stakes platform and network modernization efforts. All are meant to plug into the broader JADC2 architecture (see graphic).

The staying power of each initiative is not assured – Congress, new Defense Department appointees, and industry all have a voice. High-profile failures are sure to have a chilling effect.
However, two things are clear:
- System of systems-based architectures are gaining traction and likely to persist in a near-peer threat landscape, and
- Successful outcomes will require robust participation from both traditional industry and non-traditional entrants.
Framing the Challenge:
The nature of these architectures challenges business models optimized for a linear PPBE process that rewards well-targeted investments with the stable revenue and backlog prized by defense shareholders.
Business cases are built on the promise of returns that can be reasonably forecasted on a risk-adjusted basis. Without the revenue tail (and higher margins) associated with production and sustainment from a program of record, this model comes under pressure.
Defense companies are wrestling with a few attributes of system of systems architectures in particular:
Lack of Requirements Visibility:
Defense Department customers are unable and unwilling to articulate firm requirements for most next-generation system of systems architectures, with efforts still in studies, demonstrations, and pilots.
This is intended to allow experimentation and innovation, especially given the difficulty of pre-defining requirements for rapidly evolving, software-driven technologies.
However, this creates challenges for firms accustomed to investing based on predictable pathways to validated requirements.
Customer Ambitions to Own Greater Elements of the Technology Stack:
Increasingly, customers aim to enhance operational agility and vendor competition by owning the technical baseline for system of systems architectures.
This discussion has traditionally focused on government versus industry control of technical data packages – product drawings and engineering data that enable maintenance and upgrades of hardware.
However, as the boundaries between mission and enterprise IT blur, the discussion has evolved to highlight different visions of a digital technology stack.
One view is that the government should furnish the infrastructure and platform layer across projects. PlatformOne, built on the foundations of the Air Force’s Kessel Run and Kobayashi Maru software factories, is one example.
Vendors then deliver containerized capabilities at the application layer. Another view is that the government should contract for infrastructure (as it does with Azure Government and AWS GovCloud), focusing in-house resources on developing mission applications.
The Army’s Firestorm tactical fires optimization algorithm, tested at the first Project Convergence exercise, is an example.
In both visions, the microservices construct complicates industry’s value creation models and introduces new commercial IT competitors.
Drive Towards Enhanced Modularity and Interoperability:
Effectively fusing disaggregated sensors and data sources require a set of common interfaces to break down stovepipes and enable more powerful analytics. The Joint Staff is still struggling to define standards to underpin digital architectures with multiple classification levels.
Moreover, industry’s incentives are not aligned. In commercial markets, firms monetize the data that flows through connected networks – this motivation to modularize data is largely absent for defense contractors, given the sensitivity of their customer’s operational data.
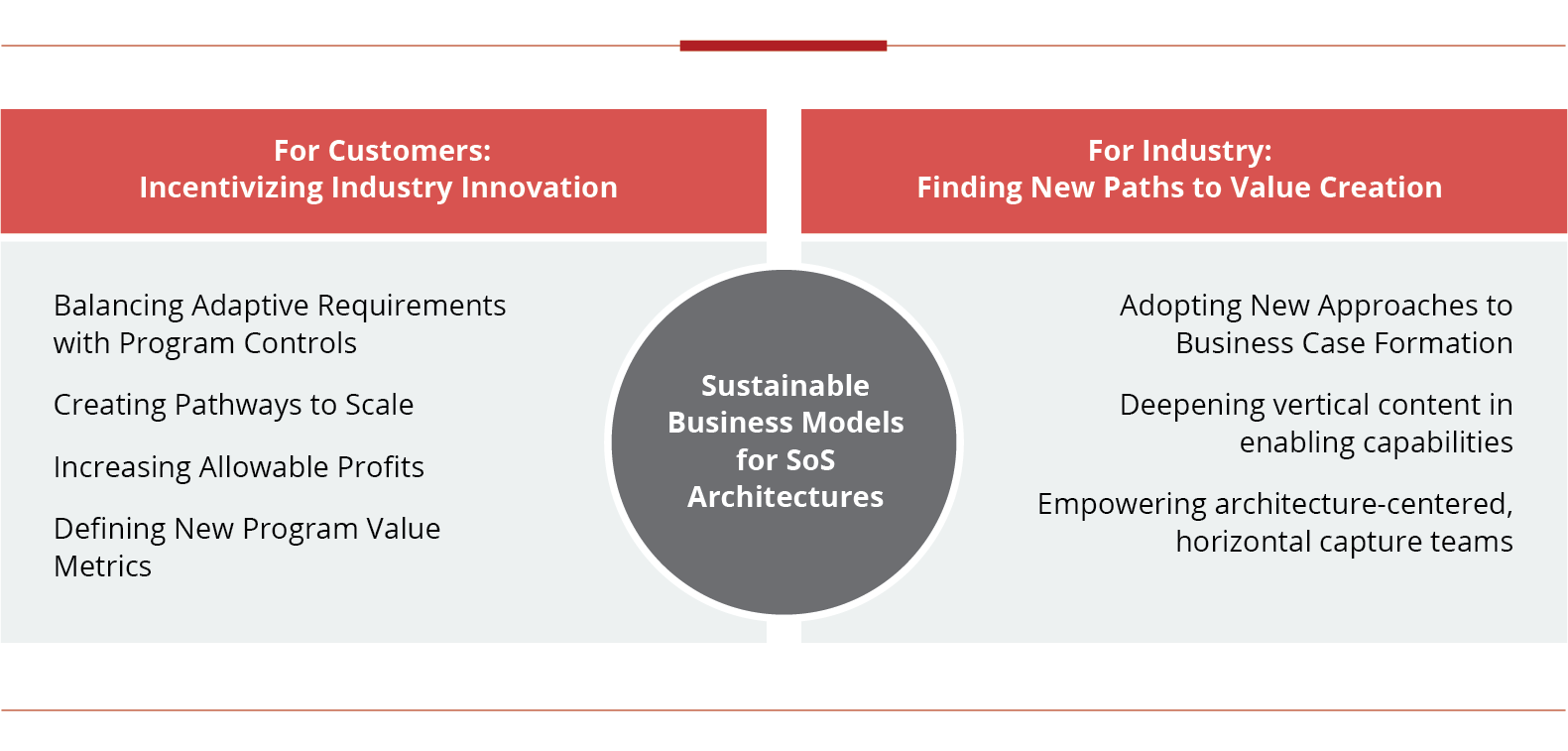
For Customers: Incentivizing Industry Innovation
As these challenges illustrate, operationalizing system of systems architectures raise fundamental questions about incentive design in our acquisition system: how can the Department attract robust industry participation and promote innovation?
Reform-minded stakeholders have increasingly championed structural improvements to each major phase of acquisition – requirements, programming & budgeting, contracting & execution, and oversight:
Requirements – Balancing Adaptive Requirements with Program Controls
The Defense Department has tried to stabilize requirements during development to prevent the moving targets that hampered programs like Future Combat Systems and Joint Tactical Radio System, even at the cost of fielding obsolescent technology.
However, the JCIDS process is ill-equipped for digital technologies requiring iterative development and continuous integration and delivery. The Defense Department’s new JCIDS-exempted acquisition pathway for software is a strong start, but it focuses at the programmatic rather than the architectural level.
Faster feedback loops for requirements should be accompanied by rapid review mechanisms that ensure updates still fit the parameters of the original operational need and do not drive significant risk.
Programming & Budgeting – Creating Pathways to Scale
Companies pursuing content in system of systems architectures need flexible pathways to scale successful demonstration and prototype contracts to recurring revenue.
Without defense primes’ multi-program portfolios and mechanisms to reimburse internal R&D, commercial firms and startups often lack the resources to bridge this gap.
Organization- or capability-centric program elements would better enable new program funds within a 2-year programming cycle (or even a fiscal year) for successfully demonstrated technology.
Contracting & Execution – Increasing Allowable Profits
Perhaps the most important incentive for investment and innovation is to increase allowable profits for development contracts from current FAR-constrained ceilings, especially given the inability of the Defense Department’s cost accounting systems to capture intangible value delivered by software-based IP.
The Department cannot expect sustainable partnerships with either the industrial base or non-traditional entrants if it preaches greater commercial risk-taking on one hand but continues to artificially constrain profit and compress franchise lifespans on the other.
Oversight – Defining New Program Value Metrics
Congress currently assesses execution against pre-determined, static acquisition baselines.
Funding and implementing system of systems architectures will require more flexible authorities for the Department – developing digital architectures should not depend in perpetuity on exemptions and patches to existing regulatory regimes.
However, securing buy in will be challenging as Congress views flexibility trading off with effective oversight.
The Department should define new metrics for value, create more frequent forums for program managers to apprise Congress of progress, and take a more intentional approach to building champions at the staff and member levels.
For Industry: Finding New Paths to Value Creation
Despite structural challenges of system of systems architectures and the uneven pace of reforms, industry cannot afford to stay on the sidelines.
Consider the counterfactual: can defense firms abstain from architecture maturation without hurting their existing positions? With the Department looking to legacy platforms and systems as billpayers for these architectures, a purely defensive position is increasingly untenable.
To outperform peers, defense firms must focus on creating sustainable business models for system of systems architectures that shareholders will accept.
This means evolving traditional organizational, marketing, investment, capture and program management practices. While there are no easy, one-size-fits-all answers, a few principles should be considered:
Adopting new approaches to business case formation:
Internal R&D and bid & proposal resources will face headwinds as growth in defense toplines slow. Firms must develop theses and adaptive roadmaps for a few high-conviction investments that align to internal competencies, while addressing enduring gaps in system of systems architectures.
This process will require adept anticipation of customer priorities and a greater degree of commercial risk-taking. However, there are ways to control this risk. Investments should maximize addressable market by aligning to multiple opportunities but targeted enough to have a realistic pathway to return.
They should be resourced and deployed iteratively to find avenues for early user feedback and incorporate mature component technologies whenever possible. Domestic and international partnerships should be considered to accelerate timetables.
In addition to seeding new positions, ongoing experimentation offers pathways to strengthen current franchises by demonstrating new use-cases for existing platforms. Plans to utilize Air Force tankers as communications relays and existing Army aircraft to host air-launched effects are just a few examples. While difficult to quantify in a traditional business case, these advantages should not be ignored when allocating resources.
Deepening vertical content in enabling capabilities:
Given the centrality of distributed sensing, networking, battle management, and command & control to SoS architectures, greater vertical content can drive potentially accretive growth.
While knee-jerk M&A should not be the answer, defense firms should examine enabling technologies to insource.
Autonomy, perception, and communications in denied environments are clear enduring needs. These technology competencies have broad applicability and depend less on program-specific business cases.
Beyond discrete mission systems, novel integration of commercial components will require systems integrators to diverge from traditional development approaches.
While pockets of the defense industry are adopting commercial processes and tools like DevSecOps and digital twins, the work of systematizing them across a large enterprise and integrating them with hardware engineering functions remains unfinished.
For most firms, delivering integrated hardware/software products with embedded machine intelligence capabilities will require a deeper technical bench.
At the compute layer, more powerful processing and machine learning enabled by specialized chip designs create opportunities to differentiate, especially with the Defense Department’s focus on assured microelectronics.
While vertically integrating down to the chipset level is unlikely, closer collaboration with suppliers and design customization can yield new capabilities.
Empowering architecture-centered, horizontal capture teams:
By their nature, system of systems architectures cut across a range of systems and capabilities. Aligning business development resources often demand coordination of capabilities, processes, and capture teams across SBUs for multi-sector firms.
Collaborating across P&L boundaries is never an easy task – effective coordination requires a lead SBU, a common view of the opportunity, sufficient resources, and engagement from corporate leaders to hold teams accountable, align incentives and metrics, and ultimately cultivate an internal culture that supports collaboration.
As with internal technology investments, these campaigns should be selectively resourced and deployed. Companies should avoid going to market with a “turnkey” kill chain solution, as SoS architectures will not align to a single vendor.
Campaign teams should coordinate enterprise interactions for key customers, quickly orienting resources and standing up capture teams for defined opportunities as they emerge.
Conclusion
Despite the obstacles facing system of systems architectures, the threats and technology shifts that are driving them will not recede.
Success will require the Defense Department’s sustained commitment and political capital as well as industry’s openness to new approaches. Neither side should expect meaningful variance in outcomes without fundamental shifts in acquisition incentives and industry behavior.
Change is difficult but playing at the margins is not an option – the status quo only benefits our adversaries.
With thanks to Kelleigh Bilms for editorial review.
Subscribe to the Avascent Proving Ground
We invite you to subscribe to the Avascent Proving Ground – Insights delivered to your inbox on critical issues shaping the Defense industry’s future.



