Addressing Zero Trust Architecture in Federal Health: What’s Next?

Globally, the amount of data created and consumed is growing exponentially. The rapid proliferation of devices, networks, and users has led to a landscape ripe for exploitation.
Current security and private measures are not nearly comprehensive enough to manage the sheer quantity of data in cyberspace.
While tools such as the cloud have enabled new services and solutions, they also create new vulnerabilities in both personal and professional data realms, including healthcare, which has led to the creation of zero trust architecture in Federal health.
Increased Risks to Individual Health Data
The healthcare industry is especially vulnerable to data breaches, phishing, ransomware, and other forms of cyberattack.
Healthcare data is a prime target for breaches because of its uniquely sensitive, highly private nature, with 45 million individual records affected in just the past year.
Earlier this year, an unauthorized user infiltrated Kaiser Permanente Health Plan of Washington and accessed nearly 70,000 patient records in just a few hours.
Not only do individuals face the risk of having personal information exposed, but data breaches can also result in tampered records, leading to potentially altered diagnoses and treatments.
These breaches are costly and dangerous – but they’re also all too common, both in the commercial health sector and in the federal landscape.
Cybersecurity in the Federal Landscape
Federal health agencies manage particularly sensitive datasets, distinctive in both sheer volume and in confidentiality requirements.
Over 6,000 hospitals report diagnostic data, occupancy rates, and new findings to the Department of Health and Human Services daily, and with the rise of COVID-19, the CDC has also assumed the responsibility of tracking infections, outbreaks, and the distribution of therapeutics.
Other operating divisions also handle massive quantities of civilian data – insurance data at CMS; clinical research data at the NIH; addiction and substance abuse data at SAMHSA – thereby necessitating a robust cybersecurity posture, which is now looking to zero trust architecture in federal health as a solution.
While HHS has taken perfunctory steps in the past to control access to its internal networks, the Biden administration has taken strides to enforce greater prioritization of cybersecurity across the entire federal civilian landscape.
Executive Order #14028, released in May 2021, called for “bold changes and significant investments” in cybersecurity, rather than incremental improvements, leading agencies to rethink their cyber strategies with tools like greater endpoint security management, privileged access management, and round-the-clock vulnerability monitoring – all of which, when put together, comprise a broader architecture known as ‘zero trust.’
What is Zero Trust?
Until recently, the mindset across most federal agencies regarding network security can be described as “trust-but-verify” approach, assuming malicious actors existed outside the system but could potentially find ways to breach the digital perimeter.
However, given the exponential growth in both data and the number of HHS employees with access to the aforementioned data types, the idea of implicit trust in internal users of a system is now outdated.
Zero Trust Architecture offers a new paradigm, one that assumes users with ill intent have already infiltrated the network; thus everyone must be repeatedly subjected to identity verification, restricting users from moving freely to different parts of the IT infrastructure in the agency’s perimeter without strong authentication protocols.
To borrow a common metaphor, previous cybersecurity approaches assumed that building a higher wall would be sufficient to keep out intruders, while Zero Trust Architecture assumes that the intruders have already scaled the wall.
As datasets become increasingly interoperable, each user requires access to certain aspects of the internal infrastructure, but must be restricted from accessing others, thereby making Zero Trust Architecture more challenging – but also more critical.
Executive Order #14028 is just one of several mandates from the White House insisting that federal agencies update their legacy systems to fit the Zero Trust Architecture paradigm – the OMB/CISA Federal Zero Trust Strategy (M-22-09) makes agencies use enterprise-wide single-sign on (SSO), one method of zero-trust authentication, and the National Security Memorandum (NSM-8) specifically calls for the implementation of the zero trust principles enumerated above.
Adoption of Zero Trust Architecture in Federal Health
While HHS still trails other federal civilian agencies – namely, the Homeland Security, Justice, and Treasury departments – in total cyber spend, it is among the highest across the entire federal landscape in terms of spending growth from GFY2017-GFY2022, indicating a distinctive shift towards prioritizing cybersecurity efforts in recent years.
While spend on cybersecurity has been slowly gaining traction over the past five years, GFY22 was the first fiscal year in which data portability, network security, and access management have been closer to headlines than footnotes in the President’s Budget Request.
This year, HHS’s budget requests $818 million to prioritize cybersecurity enhancements, a 14.4% increase from GFY22.
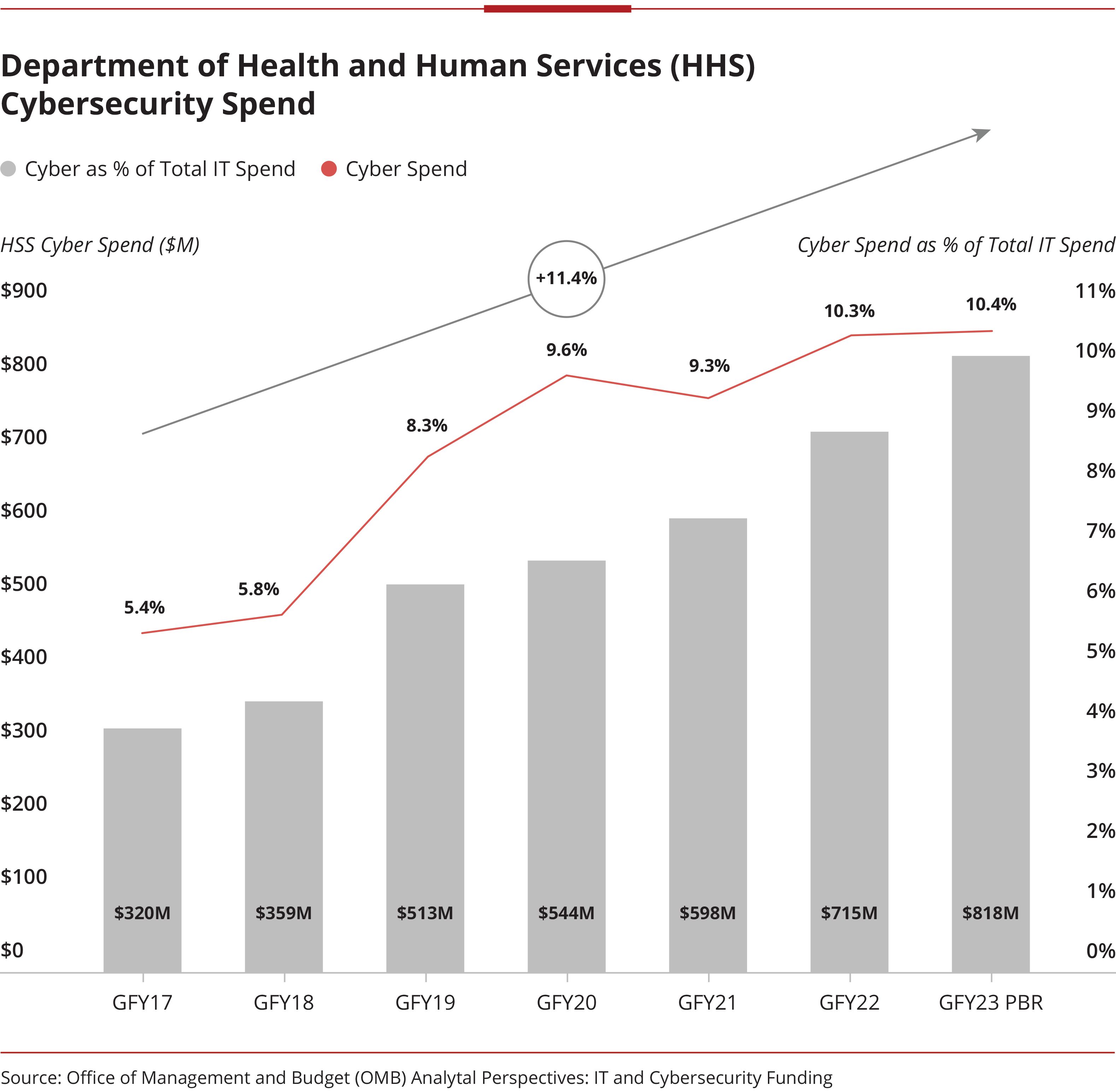
This steady increase in cyber spend is unsurprising at HHS in particular. While defense- and intelligence-focused federal agencies must prioritize the securitization of high-value assets, HHS’s focus is on the direct protection of millions of everyday Americans who place their trust in the agency to protect their personal information.
Without vigorous enforcement of security measures, their data is vulnerable to attacks, eroding the trust established.
The Zero Trust Architecture in Federal health approach has become popular at the helm of HHS – $50 million of the total $646 million in cyber spend are earmarked for Zero Trust Architecture alone – but also across multiple operating divisions.
At the helm, HHS CIO Gerald Caron has begun five foundational Zero Trust Architecture in Federal health projects that span the entire agency:
- Data mapping, in order to understand where data flow is moving
- SaaS to put monitoring in place 24/7
- A secure web gateway to send users more directly to their destination
- Maturation of ID management
- Leveraging legacy applications as part of the overarching ZTA architecture
At the OpDiv level, the FDA says it “plans to gradually implement Zero Trust Architecture principles” in its FY23 budget, while CMS’ Federal Lead for Security Architecture and Engineering, Dawn Berry, espoused the virtues of continuous information collection and verification as part of an emerging cyber strategy.
The Office of Management and Budget (OMB) has attempted to facilitate these processes for the past several years, releasing an updated policy that enables agencies to purchase logical access control systems more easily under the GSA Schedule 70 (which is transitioning under GSA MAS).
![]()
“Yes, there’s the OMB mandate that has specific things we must do, but that’s not all of Zero Trust. ZTA is about much more than what’s in the memo, and much more than just one tool off-the-shelf. It’s about data mapping and identity, but also about the users – they’re all part of a team, and ZTA is the enabler that will make them successful.”
– Gerald Caron, Chief Information Officer, HHS Office of the Inspector General
What is Next for Cybersecurity at HHS?
HHS is uniquely attuned to the most effective ways of implementing new cybersecurity measures, attempting to incorporate Zero Trust Architecture in Federal Health by shifting the cultural mindset at the agency, rather than by purchasing a slew of disparate products and hoping that an overarching strategy emerges.
Vendors can meet emerging HHS requirements in several ways:
- Remain focused on the end-user. Each operating division of HHS has a distinct mission and organizational structure. Vendors can stand out by demonstrating an understanding of that mission, and tailoring solutions to support it. In addition to considering the overarching divisions, one must also keep it simple for the users within HHS – each division is a sprawling entity with thousands of employees, and keeping every employee trained, informed, and up-to-date on the latest cybersecurity efforts is an enormous undertaking. The more intuitive – and customized – the solution, the stronger the bid.
- Offer end-to-end solutions for secure application delivery. HHS still remains constrained by budget, given the massive expense of overhauling legacy systems; thus, solutions that secure both the infrastructure at the edge and the user’s credentials offer highly compelling economies of scale.
- Incorporate robust governance policies. Zero Trust Architecture in Federal Health technology is table-stakes in today’s cyber environment; in order to reach customers, a successful ICAM solution must include procedures for cross-disciplinary incident response, ease of information sharing, and provisioning and de-provisioning of accounts on time (limiting likelihood of abuse of old credentials).
Companies working with federal health agencies can continue to support cybersecurity efforts by making Zero Trust Architecture in Federal health an inherent consideration when developing new infrastructures (e.g., hybrid cloud) and applications.
In the immediate term, solutions that facilitate the upgrade of legacy systems and increase security of existing applications without requiring complete overhaul will be highly appealing – both to HHS and the rest of the federal civilian landscape.
Subscribe to the Avascent Healthcare Pulse
We invite you to subscribe to the Avascent Healthcare Pulse – Insights delivered to your inbox on critical issues shaping the Healthcare industry’s future.



